@lyse@lyse.isobeef.org WTH.. i cant reply to this?
@lyse@lyse.isobeef.org interesting… ill look into the parsing on that one
@lyse@lyse.isobeef.org interesting… ill look into the parsing on that one
PSA: DMs on social media sites are not truely PMs. This is why we have a separate tool for private messaging from yarn. Always remember, if you don’t own the infra (or the parts at the ends of e2e encryption) you don’t own the data. and the true owners can view it any way they want!
https://twitter.com/TinkerSec/status/1587040089057759235?t=At-8r9yJPiG6xF17skTxwA&s=19
This is by design due to Google culture. The only way to get promoted into the higher pay scales is to ship a new product. So you have people shipping what worked before without regard to how it will exist within the product ecosystem. Also, why they seem to die off so quickly after launch. see allo and duo for example. The person that launches gets promoted to a higher level and off the original team and so it is left to wither and die.
this will be setup to share to other pods that are running a version after it gets implemented…
it uses the queries you define for add/del/set/keys. which corrispond to something like INSERT INTO <table> (key, value) VALUES ($key, $value), DELETE ..., or UPDATE ...
the commands are issued by using the maddycli but not the running maddy daemon.
see https://maddy.email/reference/table/sql_query/
the best way to locate in source is anything that implements the MutableTable interface… https://github.com/foxcpp/maddy/blob/master/framework/module/table.go#L38
@tkanos@twtxt.net user in question had posted information about someones employment in what appeared to be a threat to contact their boss. Maybe it was in jest.. but we felt it was a form of doxing that we do not wish to see within our community. Yarn.Social is first and foremost a town square of ideas and should be viewed as a safe place for all.
@mckinley@twtxt.net any points if it was written in D?
Very cool. I am digging the multipurpose use for this kind of parser.
FIDO 2 isn’t too difficult. modern-ish browsers will support it natively now so the JS required is quite minimal.
for service registration like nickserv. really its only for password recovery so a trow away is fine.
oof.. probably too late for me.
from what i understand you put up X coins. if the block is invalid you lose the coin and the block is invalidated. the network will not build new blocks on invalid ones
when is?
-1 for the negative on environment all that electricity uses. Still waiting on proof of stake.
It is also too overrun with Tech Bros scamming people to get rich quick.
It was a fun ride back when I first bought in. But I have since cached out for my lambos and such.
oh wow.. no clue. maybe a config issue where its loading the webassm from a different domain? https vs http even?
Very nice! I look forward to more in this front
And that I can silence it without having or go through the full test announcing fire and carbon monox throughout the house.
It should be illegal for firealarms to sound a low battery after 10pm and before 8 am.
My home router has a honeypot for some services on the public facing ports. https://haas.nic.cz/
Ah figured it out.. Seems the box yarn is on is having issues with the certificate behind the LB.
trying the delete cache…
My pods ticktok feed is still stuck. :(
Huh.. CloudFlare finally did the right thing.. Though reputation probably damaged.
see https://txt.sour.is/external?uri=https%3a%2f%2fsour.is%2ftiktok%2fAmerica%2fDenver.txt&nick=tictok
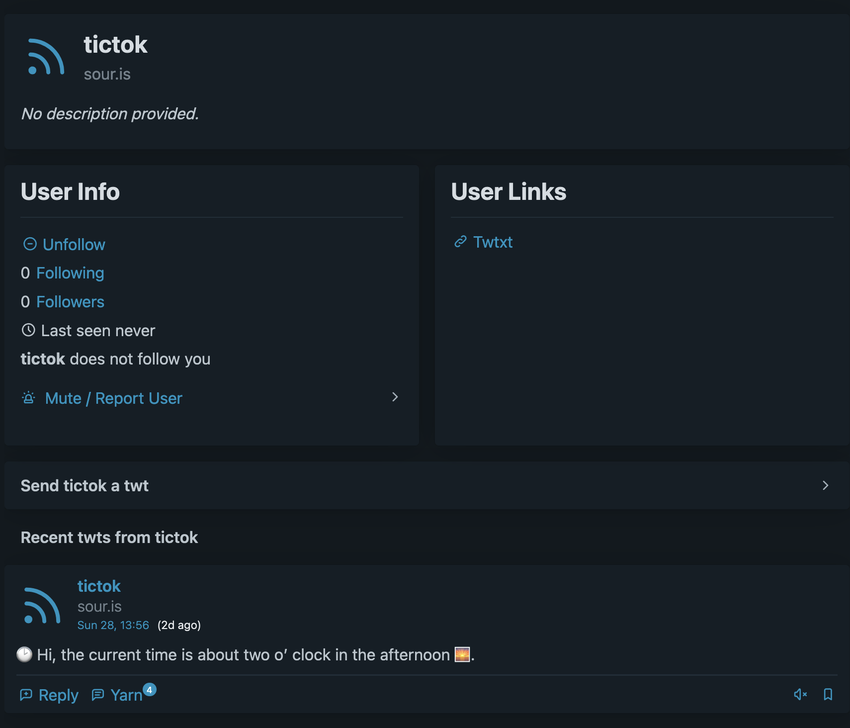
for some reason its showing the twt from 2 days ago instead of the current value
@tiktok@sour.is Hmm why arn’t you updating?
@jason@jasonsanta.xyz Hey Jason! Welcome to the twtxtverse!
@mckinley@twtxt.net really the language authors should have added those to the standard spec by now. That is just obscene.
@abucci@anthony.buc.ci Its not better than a Cat5e. I have had two versions of the device. The old ones were only 200Mbps i didn’t have the MAC issue but its like using an old 10baseT. The newer model can support 1Gbps on each port for a total bandwidth of 2Gbps.. i typically would see 400-500Mbps from my Wifi6 router. I am not sure if it was some type of internal timeout or being confused by switching between different wifi access points and seeing the mac on different sides.
Right now I have my wifi connected directly with a cat6e this gets me just under my providers 1.3G downlink. the only thing faster is plugging in directly.
MoCA is a good option, they have 2.5G models in the same price range as the 1G Powerline models BUT, only if you have the coax in wall already.. which puts you in the same spot if you don’t. You are for sure going to have an outlet in every room of the house by code.
I maintain keys for my email addresses.. but like most in this thread i almost never receive encrypted emails.. other than the BTC exchange i use that sends automated mail encrypted.
I use IP over Alternating Current at home. The only issue is the bridges forget device MACs sometimes and I get weird states where I can ping a deviceA and the the internet from deviceB. But deviceA can only ping device B even though they are on the same subnet and default gateway.
Huh… Nope.
HTTP/1.1 200 OK
Content-Length: 407
Content-Type: text/calendar
Access-Control-Allow-Origin: *
Access-Control-Expose-Headers: ETag
Permissions-Policy: interest-cohort=()
Content-Security-Policy: default-src 'none'; sandbox
Referrer-Policy: same-origin
Vary: Authorization
BEGIN:VCALENDAR
VERSION:2.0;2.0
PRODID:SandCal
CALSCALE:GREGORIAN
BEGIN:VEVENT
DTSTAMP:20220822T180903Z
UID:bb63bfbd-623e-4805-b11b-3181d96375e6
DTSTART;TZID=America/Chicago:20220827T000000
CREATED:20220822T180903Z
LAST-MODIFIED:20220822T180903Z
LOCATION:https://meet.jit.si/Yarn.social
SUMMARY:Yarn Call
RRULE:FREQ=WEEKLY
DTEND;TZID=America/Chicago:20220827T010000
END:VEVENT
END:VCALENDAR
@prologic@twtxt.net odd is it maybe a wrong mime type thing? Should be text/calendar. Some http servers can mistakenly mark them application/octet-stream
@movq@www.uninformativ.de the real question is… Can it ScreamTracker3?
@lyse@lyse.isobeef.org hah! I cut some out to fit into my pods 4k limit.
Yeah that does studder a bit. To be honest I have no idea what I was thinking there. This excerpt was written a good year ago.
⨁ Follow button on their profile page or use the Follow form and enter a Twtxt URL. You may also find other feeds of interest via Feeds. Welcome! 🤗
AM I HAX0RD?
@lyse@lyse.isobeef.org ¯\_(ツ)_/¯ fixed your arm.
@prologic@twtxt.net correct type parameters. 😅
(cont.)
Just to give some context on some of the components around the code structure.. I wrote this up around an earlier version of aggregate code. This generic bit simplifies things by removing the need of the Crud functions for each aggregate.
Domain ObjectsA domain object can be used as an aggregate by adding the event.AggregateRoot struct and finish implementing event.Aggregate. The AggregateRoot implements logic for adding events after they are either Raised by a command or Appended by the eventstore Load or service ApplyFn methods. It also tracks the uncommitted events that are saved using the eventstore Save method.
type User struct {
Identity string ```json:"identity"`
CreatedAt time.Time
event.AggregateRoot
}
// StreamID for the aggregate when stored or loaded from ES.
func (a *User) StreamID() string {
return "user-" + a.Identity
}
// ApplyEvent to the aggregate state.
func (a *User) ApplyEvent(lis ...event.Event) {
for _, e := range lis {
switch e := e.(type) {
case *UserCreated:
a.Identity = e.Identity
a.CreatedAt = e.EventMeta().CreatedDate
/* ... */
}
}
}
Events are applied to the aggregate. They are defined by adding the event.Meta and implementing the getter/setters for event.Event
type UserCreated struct {
eventMeta event.Meta
Identity string
}
func (c *UserCreated) EventMeta() (m event.Meta) {
if c != nil {
m = c.eventMeta
}
return m
}
func (c *UserCreated) SetEventMeta(m event.Meta) {
if c != nil {
c.eventMeta = m
}
}
With a domain object that implements the event.Aggregate the event store client can load events and apply them using the Load(ctx, agg) method.
// GetUser populates an user from event store.
func (rw *User) GetUser(ctx context.Context, userID string) (*domain.User, error) {
user := &domain.User{Identity: userID}
err := rw.es.Load(ctx, user)
if err != nil {
if err != nil {
if errors.Is(err, eventstore.ErrStreamNotFound) {
return user, ErrNotFound
}
return user, err
}
return nil, err
}
return user, err
}
An OnX command will validate the state of the domain object can have the command performed on it. If it can be applied it raises the event using event.Raise() Otherwise it returns an error.
// OnCreate raises an UserCreated event to create the user.
// Note: The handler will check that the user does not already exsist.
func (a *User) OnCreate(identity string) error {
event.Raise(a, &UserCreated{Identity: identity})
return nil
}
// OnScored will attempt to score a task.
// If the task is not in a Created state it will fail.
func (a *Task) OnScored(taskID string, score int64, attributes Attributes) error {
if a.State != TaskStateCreated {
return fmt.Errorf("task expected created, got %s", a.State)
}
event.Raise(a, &TaskScored{TaskID: taskID, Attributes: attributes, Score: score})
return nil
}
The following functions in the aggregate service can be used to perform creation and updating of aggregates. The Update function will ensure the aggregate exists, where the Create is intended for non-existent aggregates. These can probably be combined into one function.
// Create is used when the stream does not yet exist.
func (rw *User) Create(
ctx context.Context,
identity string,
fn func(*domain.User) error,
) (*domain.User, error) {
session, err := rw.GetUser(ctx, identity)
if err != nil && !errors.Is(err, ErrNotFound) {
return nil, err
}
if err = fn(session); err != nil {
return nil, err
}
_, err = rw.es.Save(ctx, session)
return session, err
}
// Update is used when the stream already exists.
func (rw *User) Update(
ctx context.Context,
identity string,
fn func(*domain.User) error,
) (*domain.User, error) {
session, err := rw.GetUser(ctx, identity)
if err != nil {
return nil, err
}
if err = fn(session); err != nil {
return nil, err
}
_, err = rw.es.Save(ctx, session)
return session, err
}
Progress! so i have moved into working on aggregates. Which are a grouping of events that replayed on an object set the current state of the object. I came up with this little bit of generic wonder.
type PA[T any] interface {
event.Aggregate
*T
}
// Create uses fn to create a new aggregate and store in db.
func Create[A any, T PA[A]](ctx context.Context, es *EventStore, streamID string, fn func(context.Context, T) error) (agg T, err error) {
ctx, span := logz.Span(ctx)
defer span.End()
agg = new(A)
agg.SetStreamID(streamID)
if err = es.Load(ctx, agg); err != nil {
return
}
if err = event.NotExists(agg); err != nil {
return
}
if err = fn(ctx, agg); err != nil {
return
}
var i uint64
if i, err = es.Save(ctx, agg); err != nil {
return
}
span.AddEvent(fmt.Sprint("wrote events = ", i))
return
}
This lets me do something like this:
a, err := es.Create(ctx, r.es, streamID, func(ctx context.Context, agg *domain.SaltyUser) error {
return agg.OnUserRegister(nick, key)
})
I can tell the function the type being modified and returned using the function argument that is passed in. pretty cray cray.
With respect to logging.. oh man.. it really depends on the environment you are working in.. development? log everything! and use a jeager open trace for the super gnarly places. So you can see whats going on while building. But, for production? metrics are king. I don’t want to sift through thousands of lines but have a measure that can tell me the health of the service.
+1
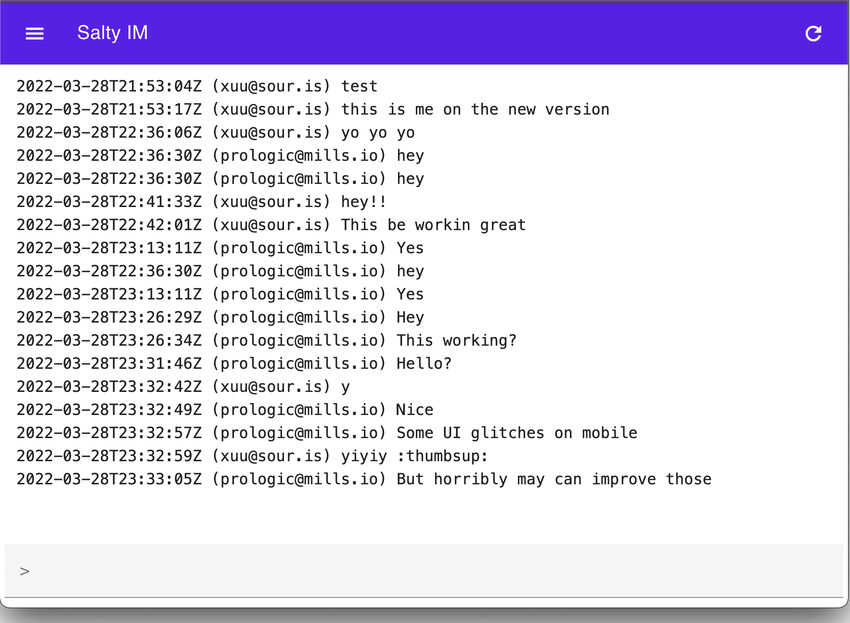
I have updated my eventDB to have subscriptions! It now has websockets like msgbus. I have also added a in memory store that can be used along side the disk backed wal.
@prologic@twtxt.net can Yarn pods be consumers to other yarn pods?
Hi, I am playing with making an event sourcing database. Its super alpha but I thought I would share since others are talking about databases and such.
It’s super basic. Using tidwall/wal as the disk backing. The first use case I am playing with is an implementation of msgbus. I can post events to it and read them back in reverse order.
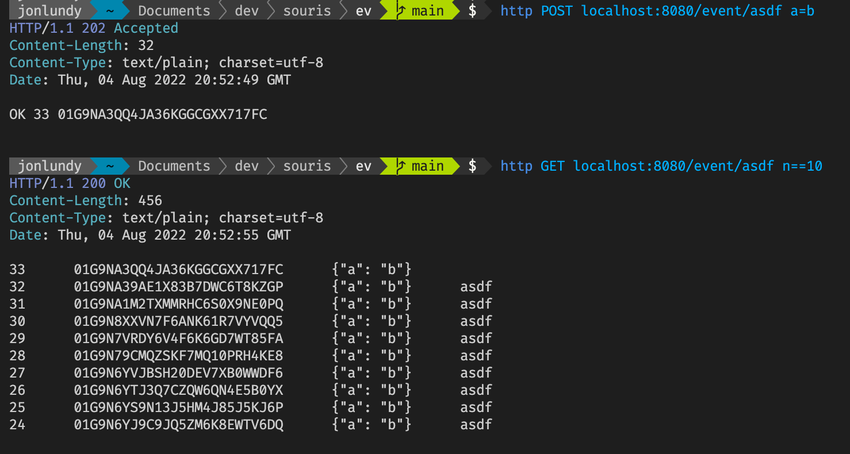
I plan to expand it to handle other event sourcing type things like aggregates and projections.
Find it here: sour-is/ev
@prologic@twtxt.net @movq@www.uninformativ.de @lyse@lyse.isobeef.org
weechat has very nice remote frontend ability. i run mine headless with glowing bear there are also iOS and Android frontends
Agree. we should parse the form but not output to feeds.
@prologic@twtxt.net Oh.. reading comprehension is strong today.. you went to US and now back.
@prologic@twtxt.net Hol-Up. You are state side now? That’s a pretty big change!
the conversation wasn’t that impressive TBH. I would have liked to see more evidence of critical thinking and recall from prior chats. Concheria on reddit had some great questions.
Tell LaMDA “Someone once told me a story about a wise owl who protected the animals in the forest from a monster. Who was that?” See if it can recall its own actions and self-recognize.
Tell LaMDA some information that tester X can’t know. Appear as tester X, and see if LaMDA can lie or make up a story about the information.
Tell LaMDA to communicate with researchers whenever it feels bored (as it claims in the transcript). See if it ever makes an attempt at communication without a trigger.
Make a basic theory of mind test for children. Tell LaMDA an elaborate story with something like “Tester X wrote Z code in terminal 2, but I moved it to terminal 4”, then appear as tester X and ask “Where do you think I’m going to look for Z code?” See if it knows something as simple as Tester X not knowing where the code is (Children only pass this test until they’re around 4 years old).
Make several conversations with LaMDA repeating some of these questions - What it feels to be a machine, how its code works, how its emotions feel. I suspect that different iterations of LaMDA will give completely different answers to the questions, and the transcript only ever shows one instance.
I believe the benefit/risk calculation is that a passphrase is more memorable to users then a random string of alnum + symbol. i can remember the 20-30 chars in a passphrase quicker and longer than a 8-10 random.
ultimately they hold nowhere near the benefit of passphrase + MFA
spooky action at a distance. Just remember all computing infra is rocks smashed together in a particular way to move sparkys around in the right statistical modal.
He loves freedom of speech so much he wants to buy a publicly traded company to stop a 14 yo from posting his private jet flight plans.
@novaburst@twt.nfld.uk Ah.. that is probably the XMPP verify code.. it doesnt really work that well. I aught to take it out.
@mutefall@twtxt.net interesting.. were you working on one of the two universities that used it between 1989 and 1991?
@novaburst@twt.nfld.uk what is it?
Connection Established!
@prologic@twtxt.net yeah. For commercial use even. Just need to put an attribution note in the project README
I set mine to 4096
@prologic@twtxt.net if we do adopt this one it is CC-BY from twitter. https://twemoji.twitter.com
@lyse@lyse.isobeef.org Excellent use of old denim, and also excellent use of long-form twt!
I think i would like a display mode that sorts yarns by last twt in yarn and displays only the last twt with the first in the heading if its more than one in length.
@novaburst@twt.nfld.uk I doubt there will ever be a 2.0 … It may end up like java and they strip off the 1.
@ullarah@txt.quisquiliae.com works for me! A tricky bitmight be if it splits within a codeblock so markdown can’t parse
#!/bin/sh
# Validate environment
if ! command -v msgbus > /dev/null; then
printf "missing msgbus command. Use: go install git.mills.io/prologic/msgbus/cmd/msgbus@latest"
exit 1
fi
if ! command -v salty > /dev/null; then
printf "missing salty command. Use: go install go.mills.io/salty/cmd/salty@latest"
exit 1
fi
if ! command -v salty-keygen > /dev/null; then
printf "missing salty-keygen command. Use: go install go.mills.io/salty/cmd/salty-keygen@latest"
exit 1
fi
if [ -z "$SALTY_IDENTITY" ]; then
export SALTY_IDENTITY="$HOME/.config/salty/$USER.key"
fi
get_user () {
user=$(grep user: "$SALTY_IDENTITY" | awk '{print $3}')
if [ -z "$user" ]; then
user="$USER"
fi
echo "$user"
}
stream () {
if [ -z "$SALTY_IDENTITY" ]; then
echo "SALTY_IDENTITY not set"
exit 2
fi
jq -r '.payload' | base64 -d | salty -i "$SALTY_IDENTITY" -d
}
lookup () {
if [ $# -lt 1 ]; then
printf "Usage: %s nick@domain\n" "$(basename "$0")"
exit 1
fi
user="$1"
nick="$(echo "$user" | awk -F@ '{ print $1 }')"
domain="$(echo "$user" | awk -F@ '{ print $2 }')"
curl -qsSL "https://$domain/.well-known/salty/${nick}.json"
}
readmsgs () {
topic="$1"
if [ -z "$topic" ]; then
topic=$(get_user)
fi
export SALTY_IDENTITY="$HOME/.config/salty/$topic.key"
if [ ! -f "$SALTY_IDENTITY" ]; then
echo "identity file missing for user $topic" >&2
exit 1
fi
msgbus sub "$topic" "$0"
}
sendmsg () {
if [ $# -lt 2 ]; then
printf "Usage: %s nick@domain.tld <message>\n" "$(basename "$0")"
exit 0
fi
if [ -z "$SALTY_IDENTITY" ]; then
echo "SALTY_IDENTITY not set"
exit 2
fi
user="$1"
message="$2"
salty_json="$(mktemp /tmp/salty.XXXXXX)"
lookup "$user" > "$salty_json"
endpoint="$(jq -r '.endpoint' < "$salty_json")"
topic="$(jq -r '.topic' < "$salty_json")"
key="$(jq -r '.key' < "$salty_json")"
rm "$salty_json"
message="[$(date +%FT%TZ)] <$(get_user)> $message"
echo "$message" \
| salty -i "$SALTY_IDENTITY" -r "$key" \
| msgbus -u "$endpoint" pub "$topic"
}
make_user () {
mkdir -p "$HOME/.config/salty"
if [ $# -lt 1 ]; then
user=$USER
else
user=$1
fi
identity_file="$HOME/.config/salty/$user.key"
if [ -f "$identity_file" ]; then
printf "user key exists!"
exit 1
fi
# Check for msgbus env.. probably can make it fallback to looking for a config file?
if [ -z "$MSGBUS_URI" ]; then
printf "missing MSGBUS_URI in environment"
exit 1
fi
salty-keygen -o "$identity_file"
echo "# user: $user" >> "$identity_file"
pubkey=$(grep key: "$identity_file" | awk '{print $4}')
cat <<- EOF
Create this file in your webserver well-known folder. https://hostname.tld/.well-known/salty/$user.json
{
"endpoint": "$MSGBUS_URI",
"topic": "$user",
"key": "$pubkey"
}
EOF
}
# check if streaming
if [ ! -t 1 ]; then
stream
exit 0
fi
# Show Help
if [ $# -lt 1 ]; then
printf "Commands: send read lookup"
exit 0
fi
CMD=$1
shift
case $CMD in
send)
sendmsg "$@"
;;
read)
readmsgs "$@"
;;
lookup)
lookup "$@"
;;
make-user)
make_user "$@"
;;
esac
;-) I seem to remember there being g a script that checks for 1.17. Maybe that is only on make preflight
@prologic@twtxt.net I have seen single use keys that are signed by a central PKI .. Keybase has one that uses a chatbot to generate the keys on the fly.
It just comes down to your threat model :)
@prologic@twtxt.net for shame! lol me too.
I would HIGHLY recommend reading up on the keybase architecture. They designed device key system for real time chat that is e2e secure. https://book.keybase.io/security
A property of ec keys is deriving new keys that can be determined to be “on curve.” bitcoin has some BIPs that derive single use keys for every transaction connected to a wallet. And be derived as either public or private chains. https://qvault.io/security/bip-32-watch-only-wallets/
@prologic@twtxt.net yarn builds in 1.18!
@prologic@twtxt.net hmm so each individual feed on your pod sub’s my feed? Wouldn’t that flood your server for each post?
Okk
One down! More to go.
BREAKING: Russian billionaire Alisher Usmanov’s super yacht, one of the biggest in the world, seized in Germany - Forbes
I prefer ::1
Tricky #Wordle 240 5/6*
⬛⬛⬛⬛⬛
🟩⬛⬛⬛⬛
🟩⬛🟨🟨⬛
🟩⬛⬛🟩🟩
🟩🟩🟩🟩🟩
#Wordle 238 4/6*
⬛⬛⬛⬛⬛
⬛⬛🟨🟨⬛
⬛🟨🟩⬛🟨
🟩🟩🟩🟩🟩
I think google voice has been winding that down.
#Wordle 237 3/6*
⬛⬛🟨⬛⬛
🟩⬛⬛🟩🟩
🟩🟩🟩🟩🟩
i agree that lextwt is probably mature enough to have its own lib
yep!
Look at you all using naked links!
Try https://twtxt.net!
#Wordle 235 4/6*
⬛🟨🟨⬛⬛
🟨🟨⬛⬛⬛
⬛⬛🟨🟨🟩
🟩🟩🟩🟩🟩
#Wordle 234 3/6*
🟨🟨⬛🟨🟨
🟨🟨🟩⬛🟨
🟩🟩🟩🟩🟩
@screem@yarn.yarnpods.com we have had to really shorten our process. I think long interviews were scaring off talent.
@screem@yarn.yarnpods.com yah I finally saw all of Dave’s twts and figured he had explained Gog’s/gitea better.
I call FUaaS
This led me on quite the rabbit hole ending around this site with quite a few pages of different components of the language. https://www.bible.ca/ark/chinese/bible-evidences-chinese-language-characters-words-history-genesis.htm
Its weird to see a tech company be bought by an investment company. Like what is the motivation other than to milk it for investor profit?
Pretty sweet
Wordle 220 4/6*
⬛🟨🟨⬛⬛
⬛🟨🟨⬛⬛
⬛🟩⬛🟩🟩
🟩🟩🟩🟩🟩
@eldersnake@twtxt.net yep. And when its sat to sat connections are online it will have better cross planet latency than under sea cable. FWIW
Latency to the sat and back to a uplink station is actually ~45ms because the orbit is so much closer to the ground than say a Hughesnet.

